|
|
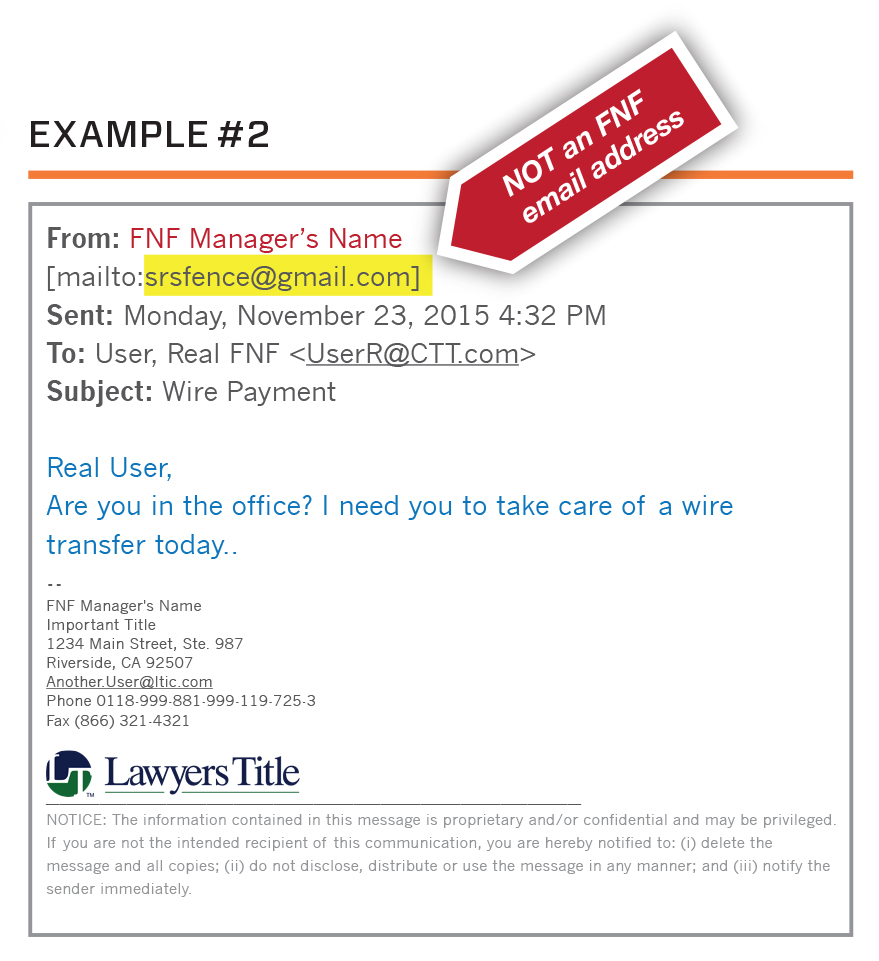
Recent cyber related incidents affecting the Company involve email "spoofing" of FNF management, including some senior level executives. The goal of the scheme is to induce an employee to wire funds at the direction of a fraudster impersonating a Company executive.
This is a pretty straight forward Business Email Compromise (BEC) scheme. Notice the display name in the examples reflects an employee name, but the email address is a Gmail™ account. Thankfully, the employees who received the emails noticed the red flags and reported them to the Fraud/Compliance Department.
Attempts have been made to compromise the email accounts of high–level business executives (CFO, CTO, etc.). To date, this has not happened at FNF. The account might be spoofed or hacked. A request for a wire transfer from the compromised account is made to a second employee within the Company who is normally responsible for processing these requests.
In some instances a request for a wire transfer from the compromised account is sent directly to the financial institution with instructions to urgently send funds to the bank. This particular version has also been referred to as "CEO Fraud," "Business Executive Scam," "Masquerading" and "Financial Industry Wire Frauds."

The Internet Crime Complaint Center (IC3) suggests the following measures to help both you personally and the Company from becoming victims:
- Only use Company Web site domain accounts.
- Be careful what is posted to social media and Company websites, especially job duties/descriptions, hierarchal information and out of office details.
- Be suspicious of email requests for secrecy or pressure to take action quickly.
- Out of Band Communication: Establish other communication channels, such as telephone calls, to verify significant transactions. Arrange this second–factor authentication early in the relationship and outside the email environment to avoid interception by a hacker.
- Digital Signatures: Both entities on either side of transactions should use digital signatures. However, this will not work with Web–based email accounts. Additionally, some countries ban or limit the use of encryption.
- Delete Spam: Immediately delete unsolicited email (spam) from unknown parties. Do NOT open spam email, click on links in the email or open attachments. These often contain malware that will give subjects access to your computer system.
- Forward vs. Reply: Do not use the "Reply" option to respond to any business emails. Instead, use the "Forward" option and either type in the correct email address or select it from the email address book to ensure the intended recipient's correct email address is used.
- Significant Changes: Beware of sudden changes in business practices. For example, if a current business contact suddenly asks to be contacted via their personal email address when all previous official correspondence has been on a Company email, the request could be fraudulent. Always verify via other channels that you are still communicating with your legitimate business partner.
|